cybersecurity
NERC's proposed internal network security monitoring standard is on track for submission to FERC after an as yet unscheduled final ballot.
NERC is taking comments through April 17 on the latest revision to its proposed internal network security monitoring standard.
Most of the U.S.’ dams lack adequate cybersecurity protections, and FERC’s resources are too limited to develop them, senators heard in committee.
PJM plans to open a solicitation window for black start service after the June 2023 request-for-proposal window did not yield fuel-assured black start generation for some transmission zones.
NERC CEO Jim Robb and E-ISAC CEO Manny Cancel shared their views on the electric reliability landscape in a media call.
CISA says its proposed cyber incident reporting requirements took into account feedback from NERC and other stakeholders.
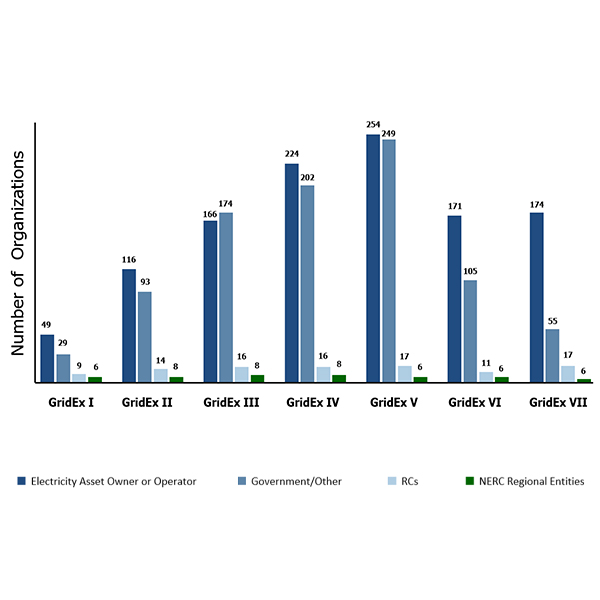
The number of participating organizations fell again in GridEx VII, the second decline in a row for the biennial security exercise.
NERC's Standards Committee moved ahead on several projects that are the subject of FERC orders at its monthly Standards Committee meeting.
Industry stakeholders were not completely sold on NERC's latest proposed cybersecurity standard.
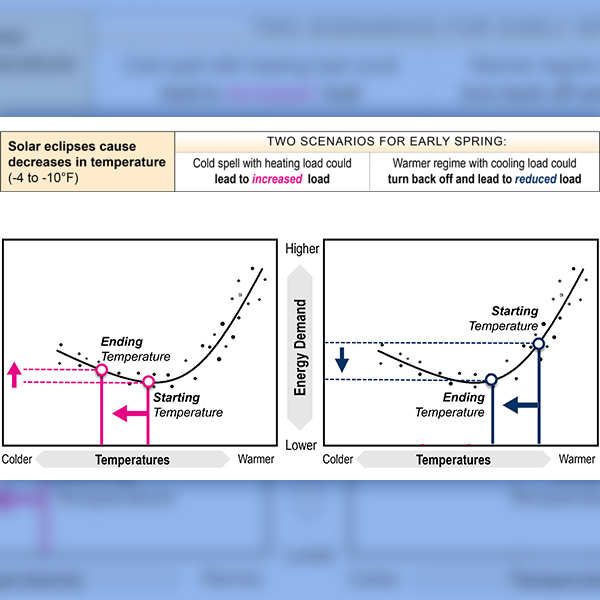
PJM's Operating Committee discussed low reserve response during a spin event in February and the possible impact April's solar eclipse could have on generation and load.
Want more? Advanced Search