E-ISAC’s Duncan Warns Cyber Threats Growing
Malware, Ransomware Attackers Becoming More Skilled
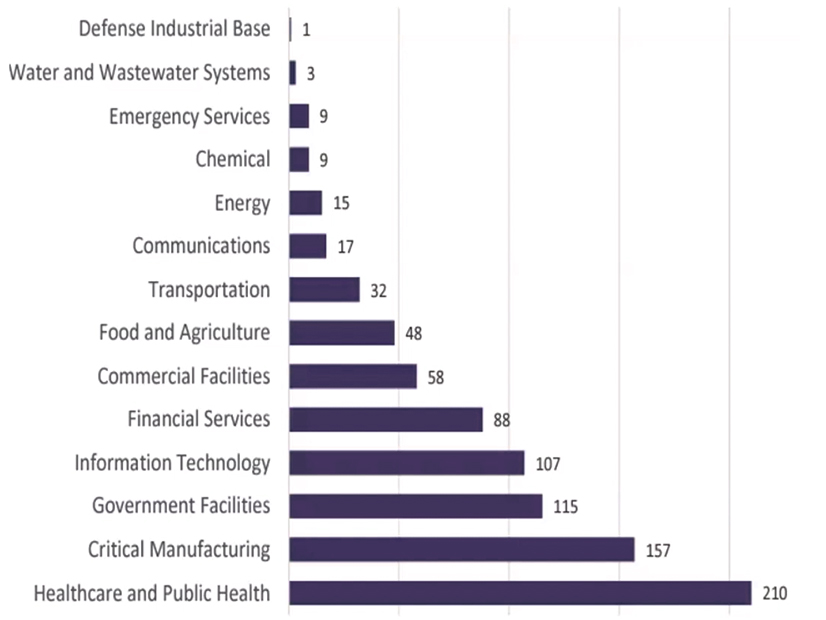
Infrastructure sectors victimized by ransomware in 2022, according to the FBI's 2022 internet crime report. | FBI
Apr 6, 2023
|
The North American electric grid remains under threat from “capable adversaries” around the world, E-ISAC staff told a forum on Thursday.


